Data Security
Data Security

-
Data Security Scanner
-
- The Data Security Scanner is a tool that enables companies and organisations as data users to conduct a quick and easy self-assessment on the sufficiency of their data security measures for their information and communications technology (ICT) systems.
- The Data Security Scanner consists of 12 questions and may take around 15 minutes to complete. Click here to get started!
-
-
Latest Updates on Data Security
-
- HKCERT - Hong Kong Security Watch Report
- HKCERT - Security Blog
- InfoSec - What’s New
- Cybersechub - Common Mistakes Made by Outsourced Contractors and Recommendations (Chinese only)
- Enhancing Data Security – Privacy Commissioner’s Office Organises Experience Sharing Session on Data Governance by Privacy-Friendly Awardees
- Reaching Out to the Community – Privacy Commissioner Interviewed by Media to Explain the Inspection Reports on the Personal Data Systems of Two Educational Institutions and the Work of the Election Task Force
- Enhancing Data Security for SMEs – Privacy Commissioner’s Office and HKPC Jointly Organise Seminar on “How Can SMEs Respond to Data Breach Incidents”
- Ensuring Information System Security Privacy Commissioner’s Office Completes the Inspections of the Personal Data Systems of Two Educational Institutions
- Enhancing Cybersecurity – Privacy Commissioner Attends Cyber Security Staff Awareness Recognition Scheme 2025/26 Recognition Ceremony
- Enhancing Data Security for Schools – Privacy Commissioner’s Office Organises Webinar on “Data Security and Risk Management in Schools”
- Enhancing Cybersecurity – PCPD Representative Attends “BugHunting Campaign 2025” Awards Gala
- Promoting AI Security and Data Security – Privacy Commissioner Publishes an Article on Hong Kong Lawyer
- Building National Cybersecurity – Acting Privacy Commissioner Attends 2025 China Cybersecurity Week Hong Kong and Macao Sub-forums
- Building National Cybersecurity – PCPD’s Representative Delivers Speech at 2025 China Cybersecurity Week Sub-Forum
-
-
Data Breach Notifications
-
What is a Data Breach?
A data breach is generally regarded as a suspected or actual breach of the security of personal data held by a data user, which exposes the personal data of data subject(s) to the risk of unauthorised or accidental access, processing, erasure, loss or use. It may amount to a contravention of Data Protection Principle 4 – security of personal data of the Personal Data (Privacy) Ordinance (Chapter 486 of the Laws of Hong Kong) (PDPO).
Submit a Data Breach Notification
A data breach notification is a formal notification given by the data user to the relevant parties including the affected data subjects and regulators such as the PCPD. A notification should generally be given as soon as practicable after becoming aware of the incident, regardless of the progress of any internal investigation.
For submitting a data breach notification to the PCPD, please visit our “Data Breach Notification” webpage.
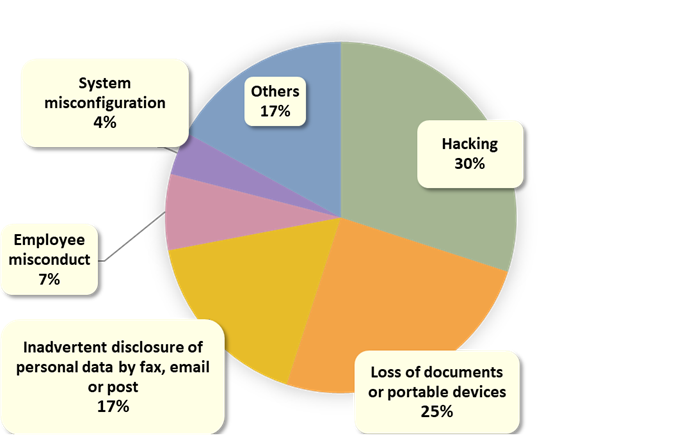
Classification of Cases in 2024
Data Breach Response Plan
A data breach response plan should set out how an organisation will respond in the event of a data breach. A comprehensive data breach response plan ensures a quick response to and effective management of a data breach, which may substantially minimise and contain the impact of the breach.
Essential Elements of a Data Breach Response Plan
- Description of what constitutes a data breach
- Internal incident notification procedure to alert senior management, the data protection officer and/or the data breach response team
- Designation of the roles and responsibilities of the data breach response team members
- Contact details of data breach response team members
- Risk assessment workflow to assess harm to affected data subjects
- Containment strategy for containing and remedying the breach
- Communication plan to determine whether and how data subjects, regulatory authorities and/or other relevant parties should be notified
- Investigation procedure for investigating the breach and reporting to senior management
- Record-keeping policy to properly document the incident
- Post-incident review mechanism to identify improvement to prevent recurrence
- Training or drill plan to ensure all relevant staff can follow the procedures properly when dealing with a data breach
Handling Data BreachesStep 1: Immediate gathering of essential informationStep 2: Containing the data breachStep 3: Assessing the risk of harmStep 4: Considering giving data breach notificationsStep 5: Documenting the breachFor details, please refer to the “Guidance on Data Breach Handling and Data Breach Notifications” and its Pamphlet.
Recommended Data Security Measures for Information and Communications Technology
- Data governance and organisational measures
- Risk assessments
- Technical and operational security measures
- Data processor management
- Remedial actions in the event of data security incidents
- Monitoring, evaluation and improvement
-
Other considerations
-
-
Requirements under the PDPO
-
Requirements on Data Security
Data Protection Principle (DPP) 4(1) of Schedule 1 to the PDPO requires a data user to take “all practicable steps” to ensure that any personal data held by it is protected against unauthorised or accidental access, processing, erasure, loss or use having particular regard to:- the kind of data and the harm that could result if any of those things should occur;
- the physical location where the data is stored;
- any security measures incorporated (whether by automated means or otherwise) into any equipment in which the data is stored;
- any measures taken for ensuring the integrity, prudence and competence of persons having access to the data; and
- any measures taken for ensuring the secure transmission of the data.
According to section 2(1) of the PDPO, “practicable” is defined as “reasonably practicable”. It is incumbent upon a data user to show that, in the event of personal data breaches, all reasonably practicable steps have already been taken to safeguard the security of personal data. What “reasonably practicable” steps are will hinge on the facts of each case.
Other Relevant Requirements
While DPP 4 creates an explicit legal requirement on the security of personal data, other provisions of the PDPO also have a bearing on data security. On the cardinal principle of data minimisation, DPP 1(1) provides that only an adequate but not excessive amount of personal data should be collected in relation to the purpose for which data is collected. It can be generally understood that the lesser amount of data is collected or held by a data user in the first place, the lesser exposure to security risk there may be in future.
On data retention, DPP 2(2) requires a data user to take “all practicable steps” to ensure that personal data is not kept longer than is necessary for the fulfilment of the purpose (including any directly related purpose) for which the data is or is to be used. Similarly, section 26 of the PDPO requires a data user to take “all practicable steps” to erase such personal data when the data is no longer required (subject to prescribed exceptions). Implementing data retention policies to ensure the timely deletion of personal data that is no longer needed can help reduce the risk of data breaches. The less data held by a data user, the less exposure to attack and vulnerability.
DPP 2(3) and DPP 4(2) require data users to adopt contractual or other means to ensure that any data processor engaged by them also complies with similar requirements in respect of data security and data retention.
-
-
Relevant Cases
-
- 2025
-
2024
- A former teacher accidentally shared a file containing personal data of students to the entire school on a cloud-based drive
- Unauthorised access of personal data held by a clinical centre
- Safeguarding clients’ personal data security under Work-from-Home Arrangements
- Storing clients’ documents and ex-employee’s personal data in outsourced storage facilities
- Whether customers’ personal data could be stored in a cloud system outside Hong Kong
- An online store sent invoices containing personal data to customers via unencrypted weblinks
- Mobile Wi-Fi device rental company took inadequate security measures to protect customers’ personal data
-
2023
- A folder that contained personal data of students and parents was accidentally disposed
- A staff member of a sports organisation accidentally uploaded and transmitted the personal data of event participants
- An educational institution’s improper password management led to unauthorised access to the personal data of students and parents
- Unencrypted documents containing personal data were sent to an incorrect email address
-
2022
- Loss of notebook computer under work-from-home arrangements
- Restaurants took inadequate security measures to protect customers’ information
- Staff of a property management company disclosed the personal data of residents when using recycled paper
- A telecommunications company accepted a HKID Card that had been declared lost by a customer
- An employer posted a list containing the personal data of staff who were to undergo virus testing
- 2021
- 2020
-
2019
- Recruitment platform wrongfully sent out emails containing CV information
- Unauthorised circulation of confidential documents containing personal data in social media network
- A staff member expressed his political views to members through membership communications without his employer’s consent
- Dental clinic displaying other patient’s medical record to a patient and requesting a patient to send his medical record by mobile phone
- Suspected unauthorised access to computer system of Accident & Emergency Department and disclosure of patients’ personal data to law enforcement agency by medical staff (Chinese only)
- Installation of CCTV in public corridors relating to the security of a residential building
- 2018
-
-
Educational Information
-
-
Guidance Note
- Guide to Getting Started with Anonymisation
- Guidance on Cloud Computing
- Guidance on Data Breach Handling and Data Breach Notifications
- Guidance Note on Data Security Measures for Information and Communications Technology
- Guidance on Protecting Personal Data Privacy in the Use of Social Media and Instant Messaging Apps
- Guide to Data Protection by Design for ICT Systems
- Leaflet/Booklet
- Poster
-
Report
- Investigation Report "Data Breach Incident of Adastria Asia Co., Limited"
- Investigation Report "Data Breach Incident of Kwong’s Art Jewellery Trading Company Limited and My Jewelry Management Limited"
- Investigation Report "Privacy Commissioner’s Office Published a Report Relating to Eight Personal Data Security Incidents"
- Investigation Report "Data Breach Incident of ImagineX Management Company Limited"
- Investigation Report “Data Breach Incident of Oxfam Hong Kong”
- Investigation Report “Data Breach Incident of the Electrical and Mechanical Services Department”
- Hong Kong Enterprise Cyber Security Readiness Index and AI Security Survey 2024
- Investigation Report “Data Breach Incident of the South China Athletic Association”
- Investigation Report “Ransomware Attack on the Information Systems of The Council of the Hong Kong Laureate Forum Limited”
- Investigation Report “Ransomware Attack on the Servers of The Hong Kong Ballet Limited”
- Investigation Report “Ransomware Attack on the Information Systems of the Consumer Council”
- Investigation Report “Ransomware Attack on the Information Systems of Hong Kong Cyberport Management Company Limited”
- Concerns on Electronic Food Ordering at Restaurants” (Chinese version only)
- Hong Kong Enterprise Cyber Security Readiness Index and Provacy Awareness Survey 2023
- Comparison of Privacy Settings of Social Media (Chinese only)
-
Articles
-
PCPD's Articles
- Getting Started with Anonymisation: A Practical Guide from the PCPD and Asia Pacific Privacy Authorities
- Safeguarding Personal Data Privacy in the Digital Age with PCPD’s Guidance on Cloud Computing
- Safeguarding Data Security to Stay Competitive
- Safe Use of Smartphones and Social Media Starts Today
- Safeguarding Data Security in Hong Kong: A Call to Action
- Data Security Must be Enhanced to Foil Threats
- Data Security at the Heart of the Digital World
- Your Personal Information is Not Safe when You Shop Online
- PCPD’s Updated Guidance on Data Breach
- AI's Tipping Point: A Reminder on the Importance of Privacy and Ethics
- Navigating Personal Data Privacy and Security in the Age of Digitisation
- Tech Firms Need to Develop AI Ethically and Responsibly
- Guidance on Data Security - Heightened Importance of Data Security Amid Increased Cyberthreats
- Personal Data Protection in the Digital Era
- Work-from-home Brings New Challenges to Data Protection
-
Other Articles
- Data loss prevention (DLP): An in-depth guide for security teams
- Cybersec Infohub - API Security Configuration Error (Chinese only)
- HKCERT - HKCERT Releases Annual Information Security Outlook and Forecast Next Level Phishing Attacks Difficult to Distinguish Hackers Exploit AI for Crimes Could Become a New Normal
- The Hong Kong Police Force CyberDefender - Reminder on WhatsApp Account Hijacking (Chinese only)
- Calibrating Expansion: 2023 Annual Cybersecurity Report
-
PCPD's Articles
-
Video
- PCPD + HKPC Data Security Training Series for SMEs - Seminar on “Prevention of Cyber Attacks for SMEs”
- PCPD x HKIRC Education Video - 3rd episode “Safely Using Artificial Intelligence in the Workplace”
- PCPD x HKIRC Education Video - 2nd episode “Handling of Data Breach Incidents”
- Seminar on “AI and Privacy Protection: Balancing Innovation and Safety”
-
Seminar on “Lessons from Data Breach Cases and Recommended Data Security Measures”
- Seminar on “Lessons from Data Breach Cases and Recommended Data Security Measures”: Ms Ada CHUNG Lai-ling, Privacy Commissioner for Personal Data (Cantonese only)
- Seminar on “Lessons from Data Breach Cases and Recommended Data Security Measures”: Mr Brad KWOK, Chief Personal Data Officer (Compliance & Enquiries) of PCPD (Cantonese only)
- PCPD x HKIRC Education Video - 1st episode “Protect Personal Data”
- Six Data Protection Principles under the Personal Data (Privacy) Ordinance - DPP 4 - Data Security Principle (Cantonese only)
-
Seminar on “Cybersecurity in Web 3.0 and Data Breach Handling”
- Chief Personal Data Officer (Acting) (Compliance & Enquiries) of PCPD, Mr Brad KWOK (Cantonese only)
- Security Consultant of the HKCERT, Mr Lawrence LAW (Cantonese only)
-
Webinar on “Data Security Management in the Cyber World – Practical Tips on Personal Data Security and Incident Response”
- Chief Personal Data Officer (Acting) (Compliance & Enquiries) of PCPD, Mr Brad KWOK (Cantonese only)
- Security Consultant of the HKCERT, Mr NG Yu-on (Cantonese only)
- “Learning and Teaching Privacy on Social Media” Online Forum (Cantonese only)
-
Webinar on “Social Media and You” (Excerpt) (Cantonese only)
- Ms Ada CHUNG Lai-ling, Privacy Commissioner for Personal Data, Hong Kong (Cantonese only)
- Associate Dean (External Affairs), Faculty of Engineering; Professor, Department of Systems Engineering & Engineering Management and Director of Centre of Innovation and Technology of The Chinese University of Hong Kong Professor WONG Kam Fai (Cantonese only)
-
Presentation Deck
- Webinar on “Data Security and Risk Management in Schools”
- CUHK LAW – Tencent Research Institute Cyberlaw Forum (Chinese only)
- Webinar on “Evolving Hong Kong Personal Data Privacy and Cybersecurity Risks and the Implications on Cyber Insurance”
- Seminar on “Prevention of Cyber Attacks for SMEs”
- Seminar on “Cybersecurity: Addressing Cyber Crime and Protecting Privacy” (Chinese only)
- 2025 Aggiornamento (Study Camp) for the Clergy: “Tips to Collect and Handle Personal Data” (Chinese only)
-
Seminar on “Preventing and Handling Data Breach Incidents and Enhancing Data Security Measures for the Education Sector”
- Chief Personal Data Officer (Acting) (Compliance & Enquiries) of PCPD, Mr Brad KWOK (Chinese only)
- Mr CHU Ka-tim, Chairman of the Hong Kong Association for Computer Education (HKACE) and Principal of Shatin Pui Ying College, and Mr FONG Ting-hei, Co-opted Council Member of the HKACE and Vice Principal of Pope Paul VI College (Chinese only)
- CPD Carnival 2024 (Chinese only)
- Law Lectures for Practitioners 2024
- Directors’ Symposium 2024: “Data Breach Incidents and Precautionary Measures”
- 2024 China Cybersecurity Week Macao Sub-forum on Personal Data Protection (Chinese only)
- Seminar on recommended measures to enhance data security and to handle data breaches
- Seminar on “Lessons from Data Breach Cases and Recommended Data Security Measures”(Chinese only)
- Build a Secure Cyberspace 2024 “Together, We Create a Safe Cyberworld” Webinar (Chinese only)
- Gathering of AmCham HK
- Seminar on Cybersecurity and Data Breach Handling
- Guest lecture entitled “Safeguarding Data Security Amid Increasing Cyberattacks” at the School of Law of the City University of Hong Kong
- MPF Symposium 2023
- Seminar on “Safe Use of WhatsApp and Social Media Platforms”
- Seminar on “Enhancing Data Security to Prevent Cyber Attacks”
- Practising Governance Annual Conference 2023 “How to Uphold Data Governance Standards in a Data Breach”
- Hong Kong International Computer Conference 2023 “AI for Economic Development and Social Good”
- Build a Secure Cyberspace 2023 “Protect Your Online Identity” Seminar
- Seminar on “Cybersecurity in Web 3.0 and Data Breach Handling”
- Information Technology Security Seminar organised by the Information Technology Resource Centre of the Hong Kong Council of Social Service (Chinese only)
- Seminar on “Privacy Risks and Opportunities of Digital Marketing” organised by Federation of Hong Kong Industries
- 49th meeting of the Business Facilitation Advisory Committee (Chinese only)
- Practising Governance Annual Conference 2022 “Managing Privacy Risks, Adopting Best Practices and Way Forward”
- Webinar on “Data Security Management in the Cyber World – Practical Tips on Personal Data Security and Incident Response”
- Luncheon Meeting of the Hong Kong Institute of Directors “Data Privacy Pitfalls and Tips for Directors” Presentation
- “Learning and Teaching Privacy on Social Media” Online Forum (Chinese only)
- The Hong Kong Chartered Governance Institute's 23rd Annual Corporate and Regulatory Update
- Seminar on “Personal Data Protection and Internet Security” organised by The University of Hong Kong
- The Hong Kong Chartered Governance Institute's 22nd Annual Corporate and Regulatory Update “Data Protection for Governance Professionals”
- Safe and Secure – Webinar on “Using Instant Messaging and Social Media Apps Properly” by Federation of Hong Kong Industries (Chinese only)
-
Guidance Note
-
-
News and Activities of Data Security
-
2025
- Enhancing Data Security – Privacy Commissioner’s Office Organises Experience Sharing Session on Data Governance by Privacy-Friendly Awardees
- Reaching Out to the Community – Privacy Commissioner Interviewed by Media to Explain the Inspection Reports on the Personal Data Systems of Two Educational Institutions and the Work of the Election Task Force
- Enhancing Data Security for SMEs – Privacy Commissioner’s Office and HKPC Jointly Organise Seminar on “How Can SMEs Respond to Data Breach Incidents”
- Ensuring Information System Security Privacy Commissioner’s Office Completes the Inspections of the Personal Data Systems of Two Educational Institutions
- Enhancing Cybersecurity – Privacy Commissioner Attends Cyber Security Staff Awareness Recognition Scheme 2025/26 Recognition Ceremony
- Enhancing Data Security for Schools – Privacy Commissioner’s Office Organises Webinar on “Data Security and Risk Management in Schools”
- Enhancing Cybersecurity – PCPD Representative Attends “BugHunting Campaign 2025” Awards Gala
- Promoting AI Security and Data Security – Privacy Commissioner Publishes an Article on Hong Kong Lawyer
- Building National Cybersecurity – Acting Privacy Commissioner Attends 2025 China Cybersecurity Week Hong Kong and Macao Sub-forums
- Building National Cybersecurity – PCPD’s Representative Delivers Speech at 2025 China Cybersecurity Week Sub-Forum
- Reaching Out to the Healthcare Sector – PCPD Representative Speaks at the Opening Ceremony of Hospital Authority Cybersecurity Week 2025
- Webinar on “Data Security and Risk Management in Schools”
- Reaching Out to the Community – Privacy Commissioner Interviewed by Media to Explain Investigation Reports on Two Data Breach Incidents
- Privacy Commissioner’s Office Publishes Two Investigation Reports on the Data Breach Incidents of (1) Kwong’s Art Jewellery Trading Company Limited and My Jewelry Management Limited and (2) Adastria Asia Co., Limited
- Promoting Cyber Security — Assistant Privacy Commissioner Speaks at the “CUHK LAW – Tencent Research Institute Cyberlaw Forum”
- Enhancing AI Security and Data Security Office of the Privacy Commissioner for Personal Data, Hong Kong, and Personal Data Protection Bureau, Macao, Together with Seven Privacy Protection Authorities in the Asia-Pacific Region, Release “Guide to Getting Started with Anonymisation”
- Privacy Commissioner’s Office Organises “Privacy-Friendly Awards 2025” Over 150 Organisations Receive Accolades, in a Record-Breaking Year
- Reaching Out to the Community – Privacy Commissioner Interviewed by Media to Explain Eight Data Security Incidents
- Privacy Commissioner’s Office Intervenes in Eight Personal Data Security Incidents and Advocates Strengthening the Protection of Personal Data Privacy on All Fronts
- Enhancing Cyber Security – Privacy Commissioner Publishes an Article on Hong Kong Lawyer
- Reaching Out to the Community -Privacy Commissioner Interviewed by Media to Explain How the Use of AI Affects Personal Data Privacy
- The Privacy Commissioner’s Office has Completed Compliance Checks on 60 Organisations to Ensure AI Security
- Reaching Out to the Commercial Sector - Privacy Commissioner Speaks at a Meeting of the New Territories General Chamber of Commerce
- Reaching Out to the Insurance Sector – Assistant Privacy Commissioner Speaks at a Webinar Entitled “Evolving Hong Kong Personal Data Privacy and Cybersecurity Risks and the Implications on Cyber Insurance”
- Enhancing Data Security – Privacy Commissioner Publishes an Article on Hong Kong Lawyer
- Privacy Commissioner’s Office Publishes (1) Checklist on Guidelines for the Use of Generative AI by Employees and (2) Investigation Findings on the Data Breach Incident of ImagineX Management Company Limited
- Enhancing Data Security for SMEs – Privacy Commissioner’s Office and HKPC Jointly Organise a Seminar on “Prevention of Cyber Attacks for SMEs”
- Privacy Commissioner’s Office Publishes Investigation Findings on the Data Breach Incident of the Companies Registry and Commenced Compliance Check regarding Deliveroo’s Cessation of Operations in Hong Kong
- Reaching Out to Schools – PCPD’s Representative Speaks at HKASM’s Cybersecurity Seminar
- Reporting to Legislative Council – Privacy Commissioner Attends Meeting of Legislative Council Panel on Constitutional Affairs to Brief Members on PCPD’s Work in 2024
- Enhancing Data Security – Privacy Commissioner’s Office Collaborates with HKIRC to Launch the Third Episode of Promotional Video
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain the PCPD’s work in 2024
- Privacy Commissioner’s Office Reports on its Work in 2024 and Publishes Investigation Findings on the Data Breach Incident of Oxfam Hong Kong
- Privacy Commissioner’s Office Publishes Investigation Findings on the Data Breach Incident of the Urban Renewal Authority and a Guidance on Cloud Computing
- Reaching Out to the Religious Sector – Privacy Commissioner Speaks at the “2025 Aggiornamento (Study Camp) for the Clergy”
2024- Enhancing Data Security – Privacy Commissioner’s Office Collaborates with HKIRC to Launch a New Episode of Promotional Video
- Enhancing Data Security for Schools – Privacy Commissioner’s Office Organises a Seminar for the Education Sector
- Reaching Out to Social Welfare Sector – PCPD’s Representative Speaks at the 3rd SocTech Symposium 2024
- Privacy Commissioner’s Office Publishes Investigation Findings on the Data Breach Incident of the Electrical and Mechanical Services Department and the “Blind” Recruitment Advertisements Posted on the Online Platform of Jobs DB Hong Kong Limited
- Promoting Cyber Security and AI Security – Privacy Commissioner Publishes an Article on Hong Kong Lawyer
- Enhancing Cybersecurity – PCPD’s Representative Attends “Cyber Security Staff Awareness Recognition Scheme” Recognition Ceremony
- PCPD and HKPC Jointly Release “Hong Kong Enterprise Cyber Security Readiness Index” Rises by 5.8 Points Approaching the Level in Year 2022 “Human Awareness Building” Remains at Low Levels
- Reaching Out to Accounting Professionals – Privacy Commissioner Speaks at the CPD Carnival 2024
- Reaching Out to University – PCPD’s Representative Speaks on Privacy and Data Security at The Chinese University of Hong Kong
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain the Investigation Findings on a Data Breach Incident
- Privacy Commissioner’s Office Publishes Investigation Findings on the Data Breach Incident of South China Athletic Association and Launches “Data Security” Package for Schools, NGOs and SMEs
- Reporting to Legislative Council – Secretary for Constitutional and Mainland Affairs and Privacy Commissioner Attend Meeting of the Legislative Council Panel on Constitutional Affairs
- Privacy Commissioner’s Office Welcomes the Chief Executive’s 2024 Policy Address
- Enhancing Data Security – Privacy Commissioner’s Office Collaborates with HKIRC to Launch Promotional Videos
- Enhancing Cybersecurity – PCPD Representative Attends “Bug Hunting Campaign 2024” Awards Gala
- Reaching Out to Directors – Privacy Commissioner Speaks at Directors’ Symposium 2024
- Building National Cybersecurity – Privacy Commissioner Attends the 2024 China Cybersecurity Week Hong Kong Sub-forum
- Building National Cybersecurity – Privacy Commissioner Delivers Keynote Speech at 2024 China Cybersecurity Week Macao Sub-forum
- Reaching out to the Banking Sector – PCPD, Hong Kong Monetary Authority and Hong Kong Association of Banks Jointly Organise a Seminar
- Privacy Commissioner Publishes Investigation Findings on the Data Breach Incidents of (1) The Council of the Hong Kong Laureate Forum Limited and (2) The Hong Kong Ballet Limited
- Enhancing Data Security – Privacy Commissioner’s Office Reruns the Seminar on “Lessons from Data Breach Cases and Recommended Data Security Measures”
- Enhancing Cybersecurity - Privacy Commissioner Gives Keynote Speech at HKCNSA Symposium 2024
- Enhancing Cybersecurity – PCPD Participates in the “Bug Hunting Campaign 2024” as a Strategic Partner
- Enhancing Data Security – Privacy Commissioner’s Office Organises a Seminar on “Lessons from Data Breach Cases and Recommended Data Security Measures”
- Promoting Data Security – Privacy Commissioner Publishes an Article entitled “Safeguarding Data Security to Stay Competitive” at The Bulletin
- Privacy Commissioner’s Office Urges Users of Cloud Platforms to Ensure Data Security
- Safeguard Data Security • Safeguard Privacy! Privacy Commissioner’s Office Launches a Series of Promotional and Educational Activities in Privacy Awareness Week 2024
- A 40-year-old Male Arrested for Suspected Doxxing Arising from Monetary Disputes
- Enhancing Data Security – PCPD’s Representative Speaks at the Webinar Entitled “Together, We Create a Safe Cyberworld”
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain the Findings on the Data Breach Incident of the Consumer Council
- Response of the Privacy Commissioner’s Office to the Companies Registry’s Data Breach Incident
- Privacy Commissioner’s Office Publishes Findings on the Data Breach Incident of Consumer Council
- A 65-year-old Man Arrested for Suspected Doxxing of His Former Colleague
- A 22-year-old Female Arrested for Suspected Doxxing Offence Relating to Emotional Entanglements
- Safeguarding Privacy in a Digital World – Privacy Commissioner Publishes an Article entitled “Smart Use of Smartphones and Social Media Starts Today” on Hong Kong Lawyer
- Privacy Commissioner’s Office Publishes an Investigation Report on the Data Breach Incident of Cyberport
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain Two Leaflets Issued by the PCPD
- A 32-year-old Male Arrested for Suspected Doxxing Acts
- Privacy Commissioner’s Office Issues Two Leaflets on the Smart Use of Smartphones and Social Media to Protect Personal Data Privacy
- Telling a Good Hong Kong Story– Privacy Commissioner Speaks at Gathering of AmCham HK
- A 30-year-old Male Arrested for Suspected Doxxing of Former Friend
- Enhancing Data Security – Privacy Commissioner’s Office and Hong Kong Internet Registration Corporation Limited Jointly Organise a Seminar on Cybersecurity and Data Breach Handling
- Privacy Commissioner’s Office Welcomes the Passage of the Safeguarding National Security Ordinance by the Legislative Council
- Response of the Privacy Commissioner’s Office on the SCAA’s Data Breach Incident
- Privacy Commissioner’s Office Proactively Commences Inspection of the Newly Established Children’s Biobank of Hong Kong Hub of Paediatric Excellence, The Chinese University of Hong Kong
- Reaching Out to University – Privacy Commissioner Speaks on Safeguarding Data Security at City University
- Reporting to Legislative Council – Privacy Commissioner Attended Meeting of Legislative Council Panel on Constitutional Affairs to Brief Members on PCPD’s Work in 2023
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain PCPD’s Work on Data Security
- Privacy Commissioner’s Office Fully Supports the Government’s Commencement of Public Consultation and Enactment of Legislation on Basic Law Article 23
- Response of the Privacy Commissioner’s Office on the HKU Faculty of Education’s Data Breach Incident
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media
- Privacy Commissioner’s Office Reports on its Work in 2023 and Publishes a Report on “Privacy Concerns on Electronic Food Ordering at Restaurants”
- Reaching Out to the Community – Privacy Commissioner Interviewed by RTHK Radio 1’s “Open Line Open View”
- Global Data Breach Involving Various Social Media and Online Platforms Privacy Commissioner’s Office Reminds Platform Users to Stay Vigilant
- The Privacy Commissioner’s Office has Completed Compliance Checks of All Credit Reference Agencies in Hong Kong to Ensure the Data Security of Credit Reference Databases
- Response of the Privacy Commissioner’s Office on the Social Welfare Department’s Data Breach Incident
2023- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain the Two Investigation Reports
- Privacy Commissioner’s Office Publishes Two Investigation Reports
- Promoting Data Security – Privacy Commissioner Publishes an Article entitled “Safeguarding Data Security in Hong Kong: A Call to Action” on Hong Kong Lawyer
- Reaching Out to the IT Sector – Privacy Commissioner Attends the Cybersecurity Symposium 2023
- Reaching out to the Financial Sector – Privacy Commissioner Speaks at MPF Symposium 2023
- Raising Public Awareness to Combat Fraud – Privacy Commissioner’s Office Organises a Seminar on “Safe Use of WhatsApp and Social Media Platforms”
- Reaching out to the IT Sector - Representative of the PCPD Attends the Inauguration Ceremony of the Hong Kong China Network Security Association
- Reaching Out to the Community – Privacy Commissioner Interviewed by the RTHK Radio 1’s “HK2000”
- “Hong Kong Enterprise Cyber Security Readiness Index” Recorded the Largest-Ever Decline in 2023 Actions Required to Bolster Staff Awareness on Cyber Security
- Enhancing Data Security – Privacy Commissioner’s Office Organises a Seminar on “Enhancing Data Security to Prevent Cyber Attacks”
- Reaching Out to Governance Professionals – Assistant Privacy Commissioner Speaks at Practising Governance Annual Conference 2023
- Privacy Commissioner’s Office Welcomes the Chief Executive’s Policy Address 2023
- Telling a Good Hong Kong Story – PCPD Representatives Attend the 45th Global Privacy Assembly 2023
- Privacy Commissioner’s Office has Completed the Inspection of the Customers’ Personal Data System of ZA Bank Limited to Ensure Data Security
- Reaching Out to the Community – Privacy Commissioner Interviewed by the Media to Explain WhatsApp Account Hijacking
- Privacy Commissioner’s Office Urges the Public and Organisations to Guard against WhatsApp Account Hijacking
- Reaching out to the IT Sector – Privacy Commissioner Speaks at the Hong Kong International Computer Conference 2023
- Promoting Data Security – PCPD’s Representative Speaks at the Build a Secure Cyberspace 2023 Seminar
- Privacy Commissioner’s Office Recommends Organisations to Strengthen Data Security Measures to Ensure Data Security
- Privacy Commissioner’s Office’s Response to Media Enquiries on Data Breach Incident of Consumer Council
- Privacy Commissioner’s Office Publishes an Inspection Report on the Personal Data System of the Registration and Electoral Office
- Response of the Privacy Commissioner’s Office on the Cyberport’s Data Breach Incident
- Promoting Data Security – Privacy Commissioner Speaks at the Grand Opening of HKPC’s “Smart & Secure City Hall” Exhibition
- Enhancing Data Security – Privacy Commissioner’s Office Organises a Seminar on “Cybersecurity in Web 3.0 and Data Breach Handling”
- Privacy Commissioner’s Office Issues New Guidance on Data Breach Handling and Data Breach Notifications To Safeguard Data Security
- Launch of New Online Data Breach Notification Form
- Telling a good Hong Kong Story – PCPD attends the 59th Asia Pacific Privacy Authorities Forum
- Privacy Commissioner’s Office Proactively Commences Compliance Checks of All Credit Reference Agencies to Ensure the Data Security of Credit Reference Databases
- Privacy Commissioner’s Office Publishes Two Reports
- Reaching Out to Social Welfare Sector - PCPD Officer speaks at the Information Technology Security Seminar
- Reaching Out to Information Technology Sector – Head of Compliance attended the Seminar on “Privacy Risks and Opportunities of Digital Marketing” Organised by Federation of Hong Kong Industries
- Privacy Commissioner’s Office Reports on its Work in 2022 and Publishes an Investigation Report
2022- Privacy Commissioner’s Office Publishes an Investigation Report on Two Personal Data Breach Incidents of the Registration and Electoral Office
- Privacy Commissioner’s Office Publishes an Inspection Report on the Personal Data System of TransUnion
- Reaching Out to Medical and Healthcare Sector — Privacy Commissioner Explains the Requirements of the Personal Data (Privacy) Ordinance to Staff Members of the New Territories West Cluster of Hospital Authority
- Telling the World a Good Hong Kong Story Privacy Commissioner Attends the 58th Asia Pacific Privacy Authorities Forum
- Response to media enquiry on the Suspected Disclosure and Selling of Data of WhatsApp Users (Chinese only)
- Interview with Privacy Commissioner by RTHK Radio 1’s “Accountability”
- Privacy Commissioner’s Office Publishes Two Investigation Reports
- Reaching Out to Businesses – Privacy Commissioner attends meeting of the Business Facilitation Advisory Committee
- Reaching Out to Governance Professionals – Assistant Privacy Commissioner Speaks at the Practising Governance Annual Conference 2022
- Strengthening International Connections - Privacy Commissioner attends the 44th Global Privacy Assembly 2022
- Privacy Commissioner’s Office Commences Compliance Check into a Data Breach Incident of Shangri-La Group
- Enhancing Cybersecurity – Privacy Commissioner’s Office Organises a Webinar on Cybersecurity
- Reaching Out to Governance Professionals – Privacy Commissioner Spoke at the 13th Biennial Corporate Governance Conference of the Hong Kong Chartered Governance Institute
- Reaching Out to Information Security Sector – Head of Compliance attended the Information Security Summit 2022
- Privacy Commissioner’s Office Issues Guidance Note on Data Security Measures for ICT
- Reaching out to Directors - Privacy Commissioner Spoke at the Luncheon Meeting of the Hong Kong Institute of Directors
- Reaching Out to Schools – PCPD Organised the “Learning and Teaching Privacy on Social Media” Online Forum
- Response to media enquiry on a data breach incident of Celebrations Coordination Office (Chinese only)
- PCPD Publishes Two Investigation Reports and a New Edition of Guidance Note for the Property Management Sector
- Reaching out to Governance Professionals - PCPD Delivered a Presentation at the HKCGI's “23rd Annual Corporate and Regulatory Update”
- PCPD Releases Report on “Comparison of Privacy Settings of Social Media”
- PCPD Reports on its Work in 2021 and Releases an Investigation Report
- Privacy Commissioner Commenced Investigation into a Data Breach Incident Involving a Local Hotel Group
- Working from Home: Privacy Commissioner Recommends 9 Tips to Safeguard Personal Data
2021- Privacy Commissioner Received Nearly 50 Complaint Cases about the Handling of Registration Data of Visitors
- Reaching out to University – “Personal Data Protection and Information Security Awareness Week 2021” of The University of Hong Kong
- PCPD Publishes Investigation Report on Security Measures Taken by 14 Restaurants to Protect Customers’ Registration Data
- Ransomware Attack on Digital Marketing Agency’s Computer System Privacy Commissioner Commenced Investigation
- Reaching out to Enterprises – Hong Kong Productivity Council
- PCPD Publishes “Guidance on Ethical Development and Use of AI” and Inspection Report on Customers’ Personal Data Systems of Two Public Utility Companies
- Privacy Awareness Week 2021 – “Protecting Privacy in the Internet Era” Privacy Commissioner Hosts the Webinar on “Social Media and You”
- Privacy Commissioner Delivered a Presentation on Data Protection for Governance Professionals at the HKICS's 22nd Annual Corporate and Regulatory Update
- Event organised in celebration of PCPD’s 25th Anniversary – A Webinar on “Social Media and You” to provide practical guidance on protecting personal data privacy
- Facebook Provides Users with an Online Form for Enquiry of the Reports on Suspected Data Breach
- Privacy Commissioner Follows Up on the Suspected Data Breach Relating to Clubhouse Users
- Privacy Commissioner Follows Up on the Alleged Scraping and Selling of Data of LinkedIn Users
- PCPD Issues Guidance on Protecting Personal Data Privacy in the Use of Social Media and Instant Messaging Apps
- Privacy Commissioner Commences Compliance Check on Suspected Data Breach Relating to Facebook Users
- Privacy Commissioner Conducts Compliance Check as Regards the Unauthorised Access to the Email System of Nikkei
- PCPD Sets Up Enquiry/Complaint Hotline about Doxxing and Releases the Results of a Survey on Protection of Personal Data Privacy
-
-
Useful Links
-
- PCPD's Data Security Hotline: 2110 1155
- Digital Policy Office (the then Office of the Government Chief Information Officer)
- Government Computer Emergency Response Team Hong Kong
- Hong Kong Computer Emergency Response Team Coordination Centre
- Cyber Defender
- Cybersec Training Hub
- Palo Alto Networks URL Filtering — Test a Site
- FortiGuard Lab — Web Filter Lookup
- Hong Kong Applied Science and Technology Research Institute — Cyber Range
- National Computer Network Emergency Response Technical Team/Coordination Center of China
-