
paragraphs (a) to (e). The word “loss” in DPP4(1) was added by the Amendment
Ordinance to clarify that a data user is required to take similar security measures to also
prevent loss of personal data.
8.3
Of the said paragraphs (a) to (e), the “harm test” covered by paragraph (a) is an
important consideration. The security measures to be undertaken by the data user with
respect to the data held should be proportionate to the degree of sensitivity of the data
and the harm that may result from accidental or unauthorised access to such data. For
example, in respect of the personal data held by a bank about its customers, DPP4
would require a higher degree of care in handling personal data such as the bank
statements of its customers as opposed to direct marketing or promotional materials sent
to customers.
8.4
With the increasing provision of online services for consumers, such as paying utility bills
online, e-banking and online shopping, coupled with the increasing use of online
services by data users to store or transmit personal data (e.g. cloud services), data users
should take extra care to ensure system security and protection of their customers’
personal data, which is stored and transmitted online, from unauthorised or accidental
access or alteration by, for example, computer hackers or unintended users.
8.5
Given the flexibility inherent in the drafting of “all reasonably practicable steps”, it is not
surprising that the steps required of a data user may vary widely from case to case.
Nevertheless, based on the Commissioner’s experience from cases he has handled
regarding the application of DPP4, the following precautionary steps (without in any
way limiting or affecting the Commissioner’s exercise of his powers according to the
particular circumstances of each case) are generally accepted as examples of the
appropriate measures that may be taken by data users in the situations listed below:
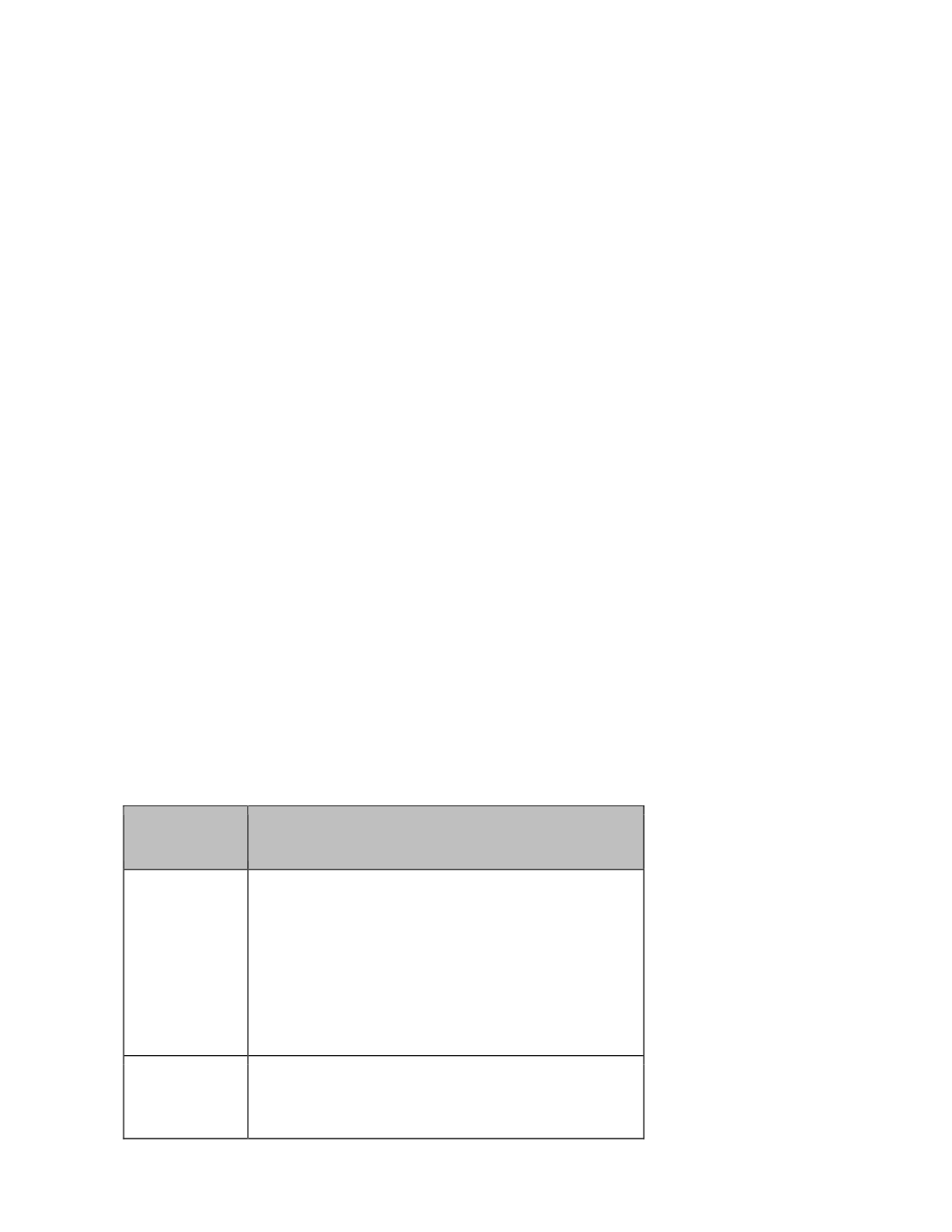
For paper documents containing personal data, data users may consider implementing the
following security measures:
Situation
Appropriate Steps
Storage of
data in
paper files
• keep files under lock and key or in a secure
area
• allow access only by authorised personnel on a
need-to-know basis
• shred files after use
• have a clear-desk policy requiring employees
to lock up sensitive papers when they are not
working on them
Transmission
of data by
fax or mail
• use sealed envelopes
• make sure no sensitive data (e.g. HKID number)
is visible through the envelope window









